Varist recently observed a phishing attack targeting a user at Northwest Radiology. Northwest Radiology is quoted as being “…one of the largest physician-owned radiology groups in central Indiana providing specialized imaging services in all areas of radiology. For more than 50 years, the Northwest Radiology team has been providing high-quality, compassionate care to patients.” Healthcare organizations continue to be subjected to phishing, which often results in the loss of sensitive information or ransomware attacks.
As is common these days, the attack specifically targets the user’s Microsoft 365 account. Below is a screenshot of the fraudulent Microsoft Office Account login page which is hosted under the web.app domain, which tries to lure the user to input his/her password.
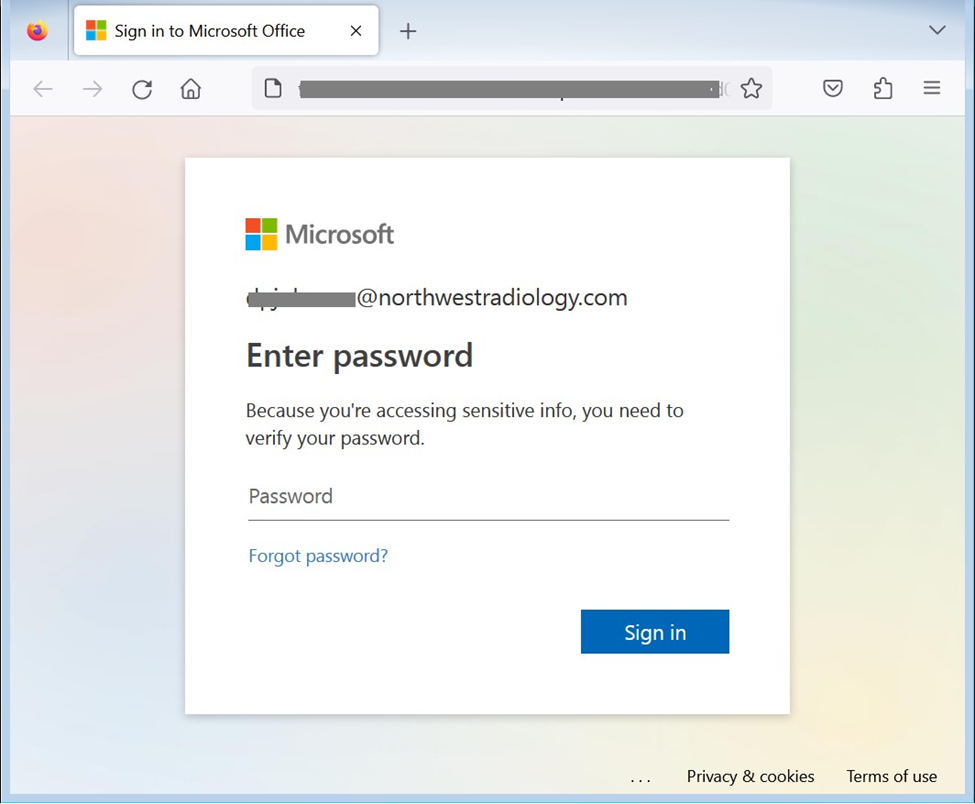
Fake Microsoft Office Account login page
This phishing page loads a JavaScript at hxxps://haeform.web.app/hae.js, which turn loads another malicious JavaScript at hxxps://haemosu.web.app/mosu/docs.js. This handles sending the user’s credentials using the Telegram app and also Deta Space as shown in the snapshot below.
App used:
hxxps://api.telegram.org/bot5841891222:AAHoK0QLA8EbC9YbtlKPbeyTupz4UMW3G78/sendMessage
hxxps://api.telegram.org/bot6018146641:AAEsrmnQB9GTRfKyRzF9HFpesGMZUaahRM/sendMessage
Information sent:
{“un”: “@northwestradiology.com”, “pw1”: “”, “correct”: “Maybe”, “IP”: “”, “whr”: “Hae Mosu”}
App used:
hxxps://idangangan-1-s6393796.deta.app/idan
Information sent:
{“u”: “@northwestradiology.com”, “p”: “”}
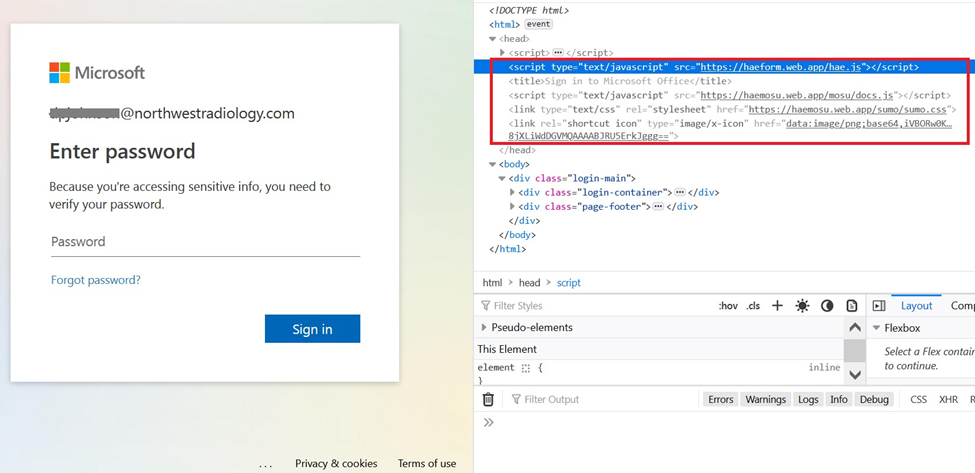
Loading of Malicious Javascript Hiding in the Web.App
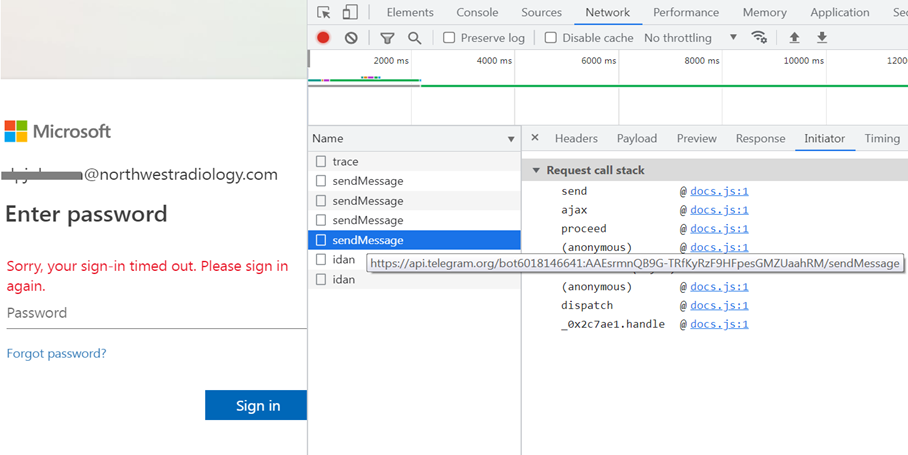
Sending of Information to Telegram App
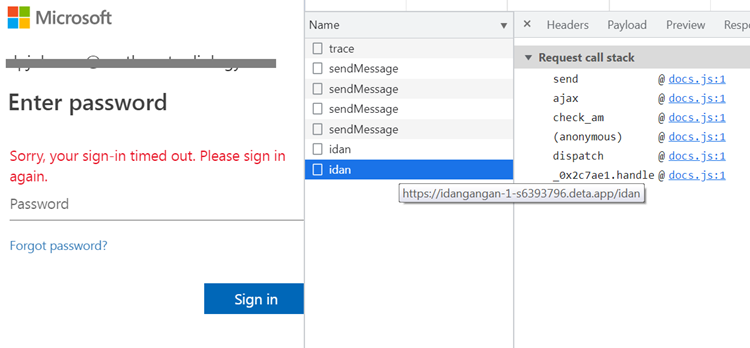
Sending of Information to Deta Space
Indicators of Compromise
| File name/URL | SHA256/Description | Varist Detection |
|---|---|---|
| df96cbe8d8ae1fd072c2f18bf237ff91600284df919c12a493d31f73d0230db9 | JS/Phish.AOA | |
| hxxps://haeform.web.app/hae.js | 253e764537327be06a6cdae31fe467f37786630cb88f05db40f06b014e0fa81b | JS/Phish.AOC |
| hxxps://haemosu.web.app/mosu/docs.js | 80994cd11d36ff815dabb69f281b7aeae47fdb276d1184db08b8b08e719d86b5 | JS/Phish.AOD |

